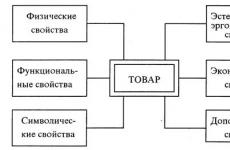
Setting up the IP according to the technical documentation. System Setup
Every 1C:Enterprise administrator knows that the task of separating user rights and correspondingly changing the working interface is one of the main tasks in implementing accounting system or the appearance of new users in it. The efficiency of work and data security depend on how well this task will be performed. Therefore, today we will talk about the features of setting up user rights and the interface in a managed application.
First of all, I would like to note the main aspects of this type of settings. Many approach this issue one-sidedly, considering them purely as a measure of protection against unauthorized access to data or their unqualified modification. At the same time, they forget about the other side of the coin: creating a simple and convenient working environment for the user. In those cases when the working user interface is overloaded with items that he does not need, the meaning of which, moreover, is not completely clear to him, a false idea arises about the excessive complexity of the program and there is a fear of making a mistake. It is clear that this does not contribute in any way to increasing the productivity of the employee.
Ideally, each employee should see only those interface elements that he needs to perform his immediate duties. Then it will be easier to work, and there will be no temptation to climb where it is not necessary. Moreover, it makes sense to perform such settings even when some subsystems are simply not used or access restriction to them is not required. This will make the interface simpler and more understandable, and, therefore, it will be easier and more comfortable for the user to work.
If we go back a little to the past, we can remember that in normal configurations Roles and Interfaces were part of the configuration and for their fine tuning it was required to enable the ability to make changes, and in the basic versions it was impossible at all.
 The disadvantages of this approach are obvious: it complicates the maintenance of infobases, and possible conflicts during subsequent updates, when changed configuration objects require changes in access rights.
The disadvantages of this approach are obvious: it complicates the maintenance of infobases, and possible conflicts during subsequent updates, when changed configuration objects require changes in access rights.
In a managed application, the permissions and interface settings have finally been moved to the user mode and are configured directly from the program interface. User rights are assigned based on their membership in access groups. Let's go to Administration - User and rights settings - Access groups - Access group profiles, where we will see the already pre-installed profiles for the main access groups.
 A user can be included in several access groups at once, in which case the total rights will be summed up. In general, everything is quite clear and familiar, except that the settings are now performed in user mode, and not in the configurator.
A user can be included in several access groups at once, in which case the total rights will be summed up. In general, everything is quite clear and familiar, except that the settings are now performed in user mode, and not in the configurator.
But if we try to find the interface settings, then a fiasco will befall us. In a managed application, the workspace interface is generated automatically based on access rights. For example, let's compare the interfaces of the Section Panel of the Administrator and the Sales Manager:
 In general - the idea is sound, there are access rights to the object - we show it in the interface, if not - we hide it. This is much better than the access violation messages that pop up in a regular application when the latter does not match the assigned interface. If you add rights to an access group or, conversely, remove them, then the interface elements associated with them will appear or disappear on their own. Comfortable? Yes.
In general - the idea is sound, there are access rights to the object - we show it in the interface, if not - we hide it. This is much better than the access violation messages that pop up in a regular application when the latter does not match the assigned interface. If you add rights to an access group or, conversely, remove them, then the interface elements associated with them will appear or disappear on their own. Comfortable? Yes.
Also, the user can independently configure his workspace within the limits of his access rights. At first glance, everything looks good, but not without a fly in the ointment. There is no mechanism to centrally configure and assign users a "default" interface in a managed application.
If we look into Administration - Users and rights settings - Personal user settings - User settings, we will see there a list of all objects whose settings have been changed by the user, but we will not be able to change them in any way.
 Those. we are offered to go directly under the user and configure the working interface on his behalf. A controversial decision, especially if there are not two or three users. Fortunately, the developers have provided the ability to copy user settings, which allows us to customize the interface of one of the users in the way we need to quickly apply the settings to everyone else.
Those. we are offered to go directly under the user and configure the working interface on his behalf. A controversial decision, especially if there are not two or three users. Fortunately, the developers have provided the ability to copy user settings, which allows us to customize the interface of one of the users in the way we need to quickly apply the settings to everyone else.
In order not to be unfounded, let's analyze practical example. In preparation for the transition to online cash registers, it was decided to automate the cash desks of a small network of dental clinics. The basis for the automation of clinics was industry software not based on 1C and not providing for the possibility of connecting a fiscal registrar, so it was decided to use the Enterprise Accounting 3.0 configuration to automate cash desks, which contains all the necessary functions.
Here we are faced with two difficulties, although if you look closely, you will find that these are two sides of the same coin. In short: the staff had never worked with 1C before, and therefore it was required to create the most easy-to-learn working environment, while protecting the information base from possible unskilled impact of the staff. A managed application allows you to simply combine business with pleasure, making it so that the user is limited, and at the same time allowing him to work comfortably without noticing the restrictions.
Let's start. First of all, you need to create a user group profile. If we open the standard profiles, we will see that there is no possibility to change them. This, in our opinion, is correct, history knows a lot of examples when, in a fit of service zeal, standard rights were shoveled to such a state that they had to be restored from the reference configuration. It can also mislead other users or administrators of this database, who expect to see standard sets of rights under standard profiles.
Therefore, we will find the most suitable profile for our tasks, in our case it is the Sales Manager, and make a copy of it, which we will give the name Cashier. Now we can customize the rights at our own discretion. However, the flat list offered by default is not very convenient to work with, unless you need to quickly find an option you already know, in most cases it is much more convenient to work with the list by enabling grouping by subsystems.
 We will not like to dwell on this issue, since the assignment of rights depends on the specific tasks facing the user, we can only advise to be prudent and not go to extremes. Remember that your task is to create a convenient and safe working environment, and not a total ban on everything possible.
We will not like to dwell on this issue, since the assignment of rights depends on the specific tasks facing the user, we can only advise to be prudent and not go to extremes. Remember that your task is to create a convenient and safe working environment, and not a total ban on everything possible.
Having created a profile, we assign an access group to the necessary users and run the program under one of them. Depending on the assigned rights, you will see an automatically generated interface.
 In principle, it’s already pretty good, but in our case, everything is just beginning. To our surprise, many users and administrators still have no idea how the Taxi interface is configured, continuing to complain about its "inconvenience".
In principle, it’s already pretty good, but in our case, everything is just beginning. To our surprise, many users and administrators still have no idea how the Taxi interface is configured, continuing to complain about its "inconvenience".
Let's go to Main Menu - View, where we will see a number of settings related to the interface.
 Let's start with section bar settings, in our case, the assortment was limited to a short list of services, so the warehouse section turned out to be superfluous, in order not to complicate and not to burden the interface, we will simply remove it.
Let's start with section bar settings, in our case, the assortment was limited to a short list of services, so the warehouse section turned out to be superfluous, in order not to complicate and not to burden the interface, we will simply remove it.
 Then, in each section, by clicking on the gear in the upper right corner, we will sequentially set up navigation and actions. Here we will also remove everything that is not necessary in everyday work, but on the contrary, we will bring to the fore what is necessary.
Then, in each section, by clicking on the gear in the upper right corner, we will sequentially set up navigation and actions. Here we will also remove everything that is not necessary in everyday work, but on the contrary, we will bring to the fore what is necessary.
 You can even compare how it was and how it became:
You can even compare how it was and how it became:
 And finally, let's configure the panels. Since we have few sections, it makes sense to move the section panel up, and the open panel down, thereby expanding the workspace horizontally, which is important for monitors with a small diagonal or 4:3 format.
And finally, let's configure the panels. Since we have few sections, it makes sense to move the section panel up, and the open panel down, thereby expanding the workspace horizontally, which is important for monitors with a small diagonal or 4:3 format.
 After completion, you should check all the settings again, it is best to do this by simulating the real actions of the cashier, which will immediately help you evaluate the convenience of working with the interface. In our case, it turned out simple and convenient workplace cashier, in any case, there were no problems with its development by the staff:
After completion, you should check all the settings again, it is best to do this by simulating the real actions of the cashier, which will immediately help you evaluate the convenience of working with the interface. In our case, it turned out simple and convenient workplace cashier, in any case, there were no problems with its development by the staff:
 Now we will enter the program again as an administrator and go to Administration - User and rights settings - User personal settings - Copy settings. Our task is to distribute the changes we have made to the remaining users of the Cashiers group. The operation itself is quite simple: select the user whose settings we copy, indicate to whom and select what exactly.
Now we will enter the program again as an administrator and go to Administration - User and rights settings - User personal settings - Copy settings. Our task is to distribute the changes we have made to the remaining users of the Cashiers group. The operation itself is quite simple: select the user whose settings we copy, indicate to whom and select what exactly.
 And finally, you can prevent the user from customizing the interface on their own, to do this, go back to the group profile and uncheck the box Saving user data.
And finally, you can prevent the user from customizing the interface on their own, to do this, go back to the group profile and uncheck the box Saving user data.
 As you can see, setting up the interface and user rights in a managed application is quite simple and, despite some shortcomings, provides administrators with much more flexibility and convenience, allowing you to quickly create convenient and secure work environments.
As you can see, setting up the interface and user rights in a managed application is quite simple and, despite some shortcomings, provides administrators with much more flexibility and convenience, allowing you to quickly create convenient and secure work environments.
Tags:
Standard solutions of 1C Enterprise for platform 8.1 provide for the differentiation of user access rights to information. On the one hand, this provides a certain degree information security of the enterprise (only the information necessary to perform its tasks is available to the user), on the other hand, it facilitates the work of users of the information system (the user does not see unnecessary information that may interfere with the quality and timely performance of his work and operate only with the data he needs).
There are 2 ways to differentiate information. At the configuration stage - more general rights and at the stage of accounting - more detailed rights to certain table records. The first is configured at the stage of system configuration by developers of applied solutions. For example, in the standard solution "1C: Accounting 8.1 for Ukraine" the following roles are provided, which should be used when creating a list of users of the information system in the "Configurator" mode:
- "Accountant" - the main role.
- « Chief Accountant» - the role should be assigned to the chief accountants and employees of the audit services of the enterprise;
- "Full rights", "Administration right", "Administration right for additional forms and processing" - these roles should be used with caution, assigning them only to those users who have the authority to administer and maintain the information system.
- "The right to connect externally" and "The right to launch external processing" - the roles are intended to ensure the possibility of using tools and mechanisms external to the information system.
It is not recommended to assign these roles to all users in a row. It is still necessary to clearly delineate the powers of users.
The list of users of the information system is formed and configured in the "Configurator" mode (menu "Administration -> Users").


The settings indicate full name user, the database access password, the interface and infobase language are selected, and its roles are assigned. A user can be assigned multiple roles at the same time.
In some standard solutions, the ability to create users also exists in the 1C Enterprise mode. To do this, in the "Users" directory there is a separate tab "DB Users" in which you can create a list of users:

After creating a new user and starting the system in the "Enterprise" mode, information about this user will be automatically entered into the "Users" directory. This operation is performed once at the first start of the infobase and is accompanied by a message about adding the user to the lookup. The list of users can be combined into groups (subgroups), since the directory supports a hierarchy. For example, you can create the following user groups: administrator, cashiers, accountants. Only those users who perform administrative functions have the rights to such actions. Access to the directory is carried out through the menu "Service -> Users". Access to the settings of the current user is carried out through the menu "Tools -> User Settings".

The code of the elements of the directory "Users" - text. As the value of the code, the “Username” is written, which is specified for this user in the Configurator in the list of system users, when logging in, the configuration determines the user who works with the system by matching the username in the Configurator and the username in the “Users” directory. It should be noted that the length of the code in the directory is 50 characters, so you should not set the user name in the configurator to more than 50 characters.
To link the “users” directory and the “individuals” directory, the requisite “ Individual". The attribute can be empty.
On the tab "Settings" are defined individual settings current user. These settings are grouped by functionality. It is recommended that you define these settings right away, since they are the ones that largely determine the behavior of the system for each user.
The default settings provide the substitution of the corresponding values in the same type details of documents, directories, reports and processing of the applied solution. With proper use of this mechanism, the time of users' work with information system objects is significantly reduced, many types of input errors are eliminated;
Functions panel settings control the behavior of the "Functions panel" service mechanism, with which you can quickly navigate through the sections of the information system and get! context help. It is especially useful to use this mechanism at the beginning of work;
The remaining settings control the behavior of the system at the level of its specific elements. For example, when you enable account correspondence control in all documents, directories and reports, when you select an account value from an accounting or tax chart of accounts, a forced selection of accounts available for selection will be carried out based on the state of a specialized information register
"Correct correspondence of accounts accounting”, which will greatly limit the capabilities of a particular user. While its neighbor's information system will behave in a completely different way (the described flag is turned off).
On the "Contact Information" tab, information about the user's contact information is entered - address, phone number, e-mail address, etc.
On the last tab “Access to objects”, the user rights are restricted at the level of records in infobase tables. It is necessary to distinguish between two information security technologies supported in the configuration:
Protection at the level of database tables;
Protection at the level of individual records of database tables (RLS);
When restricting user rights at the table level, such a user will not be able to perform any actions with the table as a whole. Such a restriction is implemented at the stage of configuring the applied solution by configuring the corresponding roles. For example, if interactive marking for deletion in the "Accounts" directory is prohibited for the "Manager" role, a specific user of the information system to whom such a role will be assigned will not be able to mark for deletion any element of the "Accounts" directory. At the same time, other operations with the directory may be available to him: viewing, creating new elements, selecting existing ones, etc. But with this approach, it is impossible, for example, to hide from such a user "foreign" counterparties (with whom other managers of the enterprise work) and data on them.

To solve such problems, the mechanism for restricting access rights at the record level (Record Level Security - RLS) is used. Application solutions provide for restriction of rights using this mechanism for certain roles, for example, in the information system "1C: Accounting 8.1 for Ukraine" for two roles:
"Accountant";
"Chief Accountant".
In this case, it is necessary to take into account the fact that some roles may not be initially assigned to a specific user.
Therefore, when restricting, for example, the role of "Chief Accountant" for the current user, no restriction may occur if this user in the "Configurator" mode is assigned only the role "Accountant" and the role "Chief Accountant" is not assigned. Thus, before using this mechanic, you need to know exactly what roles are assigned to specific users of the information system. The scope of data limited in a typical configuration includes:
Organizations from the "Organizations" directory. That is, if a user is limited to a set of organizations, he will be physically able to operate only with the data reflected for these organizations. Moreover, such a restriction will apply only to documents and reports. This mechanism does not affect directories in the standard solution (except for the "Organizations" directory itself). Thus, the unity of normative and nomenclature-reference information is ensured within the framework of the information base.
External reports and processing, connected through specialized service mechanisms;
The technically described mechanism is universal. Therefore, if necessary, it can be used when finalizing the configuration to restrict user rights according to the conditions of a specific task. For example, provide for some kind of access restriction to the items of the nomenclature list.
Physical access to the rights restriction mechanism at the level of records of database tables can be made from four objects of the applied solution:
Directory "Users". Here, on the "Access to objects" tab for the current user, a set of "permitted" objects and "permitted" actions with them in the context of each role is made
Directory "User groups". For convenience of work, the possibility of combining users into groups is provided. For these purposes, a special directory "User Groups" is used. For each directory element, you can specify a list of users, which is stored in the tabular part of the directory element. The "User Groups" directory contains one predefined element "All users". The list of users for this predefined document cannot be modified and is physically empty. Access to the directory is carried out through the menu "Tools -> User Groups" of the full interface. Additionally, in each group, its administrator must be defined, who will change the composition of the group over time. The "Access to objects" tab and the principles of working with it are similar to those discussed above for the "Users" reference book;
Directory "Organizations". Here, on the "Access to objects" tab for the current organization, a set of "allowed" users (or groups of users) and "permitted" actions by the current object in the context of each role is determined;
Regardless of the access rights settings and the roles defined at the configuration stage, information about all actions of all users when working with the infobase can be reflected in the registration log.

The logbook is called from the menu item "Service -> Logbook". Detailed description The procedure for working with the registration log is given in the book "User's Guide".
The information system has a set of controls, which includes: main menu, control panels, status bar. Collectively, this is called the user interface.
To facilitate work with the information system, several interfaces are provided:
Administrative,
Accounting,
providing various functions. The main working interfaces are "Accounting" and "Full". The “accounting” interface is poorer than the “Full” one, it lacks some commands and features.
But the principles of building both interfaces are the same. All commands in them are concentrated in the menu. Each menu is designed either to perform service or general functions, or “serves” a specific accounting section. The last type of menu may contain submenus focused on performing specific functions within such an accounting section. At the same time, the commands for calling journals and lists of documents are located higher than the commands for calling directories and other elements of the normative and nomenclature-reference subsystem. Despite the fact that when starting the system, first of all, you will have to work with the elements of the normative and nomenclature-reference subsystem of each section of the typical configuration, then during normal operational work, journals and documents will be required more often than directories. All reporting is concentrated in a separate menu.
When creating an information system user card in the "Configurator" mode, the main interface is assigned, which will be used by default when the program is launched. At the same time, it is possible to switch between interfaces during a session with the information system. This is done through the menu “Tools -> Switch interface. At the same time, it should be understood that the possibility of changing the means of managing an information system does not lead to an automatic change in access rights.
That is, situations are possible when an element can be viewed, but nothing can be done with it (an appropriate warning will be issued), since there is a corresponding restriction in the rights of any role assigned to the current user.
System "Galaktika" is a circulation-ordered product. The setup phase is mandatory when the system is put into operation; the Setup module is included in any delivery package. During the setup process, the primary filling of the main catalogs, classifiers and directories, which form a single information base and are used by all system modules, is performed. Further replenishment of the classifiers occurs in the process of operational work.
The system-wide settings allow you to select from the algorithms for performing various functions supplied with the system those that best correspond to the specifics of a given enterprise. User settings define how a particular user works. Some of them, concerning the rights of access to documents and the possibility of editing them, are set only by the system administrator.
An important element of preparing the system for operation is setting up analytics. Analysts are used both in the traditional way to set sections on accounting accounts and budget items, and to create templates for descriptions of material values with subsequent refinement of the properties of a particular material value, displaying additional fields in documents, etc.
In addition, most modules have their own tuning block. In particular, it includes functions for setting up universal hierarchical reports (Supply Management, Sales Management, Warehouse Accounting), typical business transactions (Business Operations), the format of incoming and outgoing documents (Business Document Exchange), etc. The greatest possibilities for setting up the system are provided in the modules of the Production Control circuit, which allow you to design the appearance of documents and create calculation algorithms taking into account the specifics of a particular enterprise.
The configuration functions also include the differentiation of user access rights and the configuration of corporate inter-office data exchange if the organization has remote divisions. These functions are performed with the help of special modules Access Rights and Data Replication included in the System Administration loop.
Information system of the head
For acceptance right decisions in progress economic activity managers of different levels should have information. Information can be any: planned, technological, accounting, analytical, but the main requirements for it are timeliness and reliability. The task of the Manager module is to form the necessary information about economic activity in the required context, clearly, in dynamics, with preliminary analysis.
The economic activity of the enterprise is characterized by certain indicators (detailed and aggregated). Based on economic feasibility, indicators are combined into logical groups, for example, means of production, objects of labor, personnel, production process, finance, products. When displaying information, the “traffic light” principle is applied: the values of indicators that fall into certain divisions of the rating scale (excellent/good/satisfactory/bad/dangerous/very dangerous) are highlighted in the appropriate color.
The Manager module is designed to control and manage the activities of the enterprise and includes the following functionality (Fig. 3):
formation of the goals and objectives of the manager in the language of aggregated indicators;
obtaining aggregated indicators of the economic activity of the enterprise and transferring them to the level of the head;
combination of indicators with the rating scale, calculation of deviations of actual values from planned ones;
displaying indicators with any degree of detail in the most visual and convenient way(graph, report, model, numerical data);
tracking aggregated indicators for critical deviations and options for managing critical conditions.
Rice. 4. Scheme of implementation of the module Manager
The indicators are calculated on the basis of information from the general database of the Galaktika system, the filling of which occurs during the functioning of various modules, for example, Financial and Settlement Operations (FRO), Sales Management, Production Planning, etc. In addition, they can be imported from external systems or enter manually. The calculated aggregated indicators are stored in the archive. "Threshold" values are entered in the Manager module and represent the base of regulatory and reference information of this module.
The Manager module provides various ways of presenting information:
Getting a report on the selected indicator.
Building a graph of the current state or trend analysis.
Output of indicator values in physical and/or value terms, as a percentage, in the form of a coefficient.
Calculation of deviations of actual values of indicators from planned ones.
Construction and processing of a mathematical model for assessing the behavior of the system and choosing a strategy that ensures its most efficient functioning.
In practice, each manager monitors his own set of indicators. This is determined by the external environment of the enterprise (starting from the country where it is located), and its specifics, and by what indicators the manager considers the most important. Therefore, the information system for enterprise management should be individual, based on the needs and methods of management of this manager. To provide the necessary flexibility in the implementation of this module, an integration approach with other application systems was used.
The Manager module includes tools for determining the required indicators, analytical features and calculation formulas. A mechanism for generating queries is provided to select from the database the information necessary for calculating indicators. In addition, in the process of implementation, the visual presentation of information is adjusted taking into account the composition of indicators used, as well as the range of tasks and preferences of a particular manager.
| Software name: | Information system "Code: Intranet" Information system "Techexpert: Intranet" |
| Version: | 6.3.1 |
| Trademark: | "Code" "Techexpert" |
| Scheme of work: | The information system consists of three components:
|
- Intranet.[version number].exe - setup program for the monitor and the server part of the system;
- readme.html - system installation guide;
- The registration file is a file with the .reg extension, individual for each installation of the system. Issued upon registration and contains the user's registration data;
- service.xml - contact information for service organization specialists. Information from this file is available via the hyperlink "Serving You" located on the main page of the system;
- Information product database volumes (files with .db6 extension);
- Online database update packages (files with .upo extension). Provided when needed;
- USB HASP SRM or SenseLock hardware security key. Provided when the system is protected with a hardware key. When using a HASP SRM USB dongle, a USBHASPSetup.exe driver installer is provided.
Setting order:
- Open the context menu of the banner "Launch Codex-Client" ("Launch Techexpert-Client").
If you need to save a shortcut that allows you to immediately open the main page of the virtual directory, then open the context menu of the link "Download shortcut to the client in a shared folder" corresponding to the virtual directory (may not be available in all licensing options). - Run the command "Save target as" (for IE and FireFox browsers) or "Save link as" (for Chrome browser) or "Download file from link as" (for Safari browser) or "Save link as" (for Opera browser) .
- In the dialog box, select any folder to save the shortcut (for the Chrome browser, add the “.lnk” extension to the file name in the “File name” field) and click the “Save” button.
- Launch the client using the saved shortcut. In the future, launch the client using the saved shortcut (for convenience, the shortcut can be placed on the desktop).
You can save several desktop shortcuts (for example, to work with different virtual directories) and use them to launch the client.
Attention! In case of updating the system version, the client installed on the server is updated automatically.
Installation order:
- Open the main page of the server part of the system by entering the page address in the address bar of the browser in the format: http://[network address of the server part of the system] (for example: http://172.16.0.16:8080).
- By clicking on the banner "Install Codex-Client" ("Install Techexpert-Client") download the archive kodclient.zip (texclient.zip).
- Unpack the archive kodclient.zip (texclient.zip), which contains two files:
- kodclient6.msi (texclient6.msi) - client installer
- client.ini - configuration file. This file is automatically read at client startup.
- Run the installer kodclient6.msi (texclient6.msi) and install the client following the installation wizard.
Attention! In case of updating the system version, the client installed on the local network workstation is updated automatically.
Information Systems"Code: Intranet" and "Techexpert: Intranet" can be integrated (not available for all types of licensing) into Intranet systems. To do this, just specify a link to the web interface "Code: Intranet" or "Techexpert: Intranet" from one of the pages of the Intranet system. For example, place the following html code on one of the pages:
Information systems "Code"
If the request to “Code: Intranet” or “Techexpert: Intranet” requires a special type of authorization or accounting, we recommend using a proxy server that will process requests corresponding to the type of request and then transfer them to the processing of “Code: Intranet” or “ Techexpert: Intranet. For example, if you want the server to be accessed via the https protocol, you can install the Apache Web server (www.apache.org) and the corresponding modules that provide the https and proxy protocol, install "Code: Intranet" or "Techexpert: Intranet", deny access to the port that it serves from other computers on the network, and configure the proxy server so that https requests are redirected to "Code: Intranet" or "Techexpert: Intranet".
If Codex: Intranet or TechExpert: Intranet is installed on the same computer as another Web server, you must install the system using a different port than the one used by the Web server.
To analyze the operation of the system, the Sysinfo module can be used, which is part of the system and does not require a separate installation. The Sysinfo module allows you to:
- receive reliable information about the configuration and operation parameters of the system to the extent necessary for remote diagnosis of errors and problems that have arisen, providing effective assistance and developing correct and effective recommendations.
- ensure automatic collection key configuration and system performance data into a single summary report.
- receive statistics on the number of open documents, requests made, printed documents for the current and previous calendar month.
- measure the connection speed between the client application and the server.
To obtain information using the Sysinfo module, click the link in the status bar of the running client application (at the bottom of the window), which contains information about the registration file number, etc. The "About" window will open, in which you will see the "System Information" link and the "Network Information" link.
- The system was installed normally, but the system pages are available only from the server where the installation was carried out.
As a rule, such a problem is associated with the installation of firewalls, filters or firewalls. You need to change the settings of these programs so that the port used by the system is accessible from other computers on the network.
- When you try to access the server, the system displays the message "The system requires your browser to accept cookies."
The system uses cookies to keep track of the number of users and to check the license restrictions of installed information products. This message can be caused by one of the following reasons:
- The browser settings do not allow cookies. You need to allow it to accept cookies, more detailed information see the documentation of the browser you are using;
- Some kind of anti-virus software or Internet traffic filtering is used, which removes cookies from requests. It is necessary to change the settings of this software so that cookies from the server come to the client;
- The clocks on the server and on the workstation are mismatched. If the system clock difference is more than one day, then the browser may consider the cookies received from the server as outdated and not remember them. Set the correct system clock on the server and on the client machine.
- The system displays the message "Access to the document is limited" or "The maximum number of connections allowed by the used registration file has been exceeded" when trying to access any of the pages of the information system.
These messages can be caused by one of the following reasons:
- Indeed, the number of users exceeded the number recorded in the license of any information product, or the total number of system users. In this case, purchase additional licenses.
- For some users, the browser does not save cookies between sessions with the server, and this user is counted again every time they log in to the system. You need to change your browser settings. In the system, you can see which cookies have been issued and for which addresses. To do this, in the configuration directory, follow the link that is set to the number of current users of the system. In the window that opens, there will be a table with cookie numbers, the time they were issued, and for which IP address.
- The system consumes a large amount of server RAM.
Codex: Intranet or Techexpert: Intranet is a server application that requires a relatively large amount of memory. The fact is that the information products "Kodeks" and "Techexpert" contain, as a rule, gigabytes of textual information and individual documents with illustrations can take up tens of megabytes of RAM.
To optimize interaction with the RAM of a computer acting as a server, it is recommended by means of the program itself.
- The system is slow in processing requests.
The use of a proxy server can have a significant impact on the speed of the system user. If possible, it is necessary to disable its use when accessing the server from workstations. To make this setting, contact the user's system administrator.
- The client starts slowly from a network share located on the server.
- This problem may occur when launching a client from a shortcut on a local network computer running Windows 7. Possible reason in the network interface configuration. On a computer on the local network, perform the following steps in sequence (perform all actions as an administrator):
- Install the latest network adapter drivers;
- Run command line. Run the following commands in sequence:
Netsh interface tcp set global congestionprovider = ctcp
netsh interface tcp set global timestamps = enabled
netsh interface tcp set global ecncapability=disabled
netsh interface tcp set global netdma=enabled
netsh interface tcp set global dca=enabled
- This problem can manifest itself when the client is launched using a shortcut that leads through a network resource to a shared folder located on the same computer. Create shortcuts to launch the client from a shared folder via a local resource and use them on this computer.
- This problem may occur when launching a client from a shortcut on a local network computer running Windows 7. Possible reason in the network interface configuration. On a computer on the local network, perform the following steps in sequence (perform all actions as an administrator):
- Configuring the operation of the "Professional Support Line" service for the case when access from computers on the local network to the Internet is provided by a proxy server.
- Open the administrative interface of the system. To do this, enter the address of the administrative interface in the address bar of the browser in the following format:
http://[network address of the server part of the system]/admin. - Go to the "Database update" section of the administrative interface.
- Check the "Receive update packages from the Internet" box.
- Select the type of authorization "Authorization by registration file". This must be done so that you can save your changes to the settings.
- Check the "Use custom connection settings" box.
- Check the box "Connection through a proxy server".
- Fill in the fields: "Proxy server", "User name for the proxy server", "Password for the proxy server". These parameters must be obtained from the computer network administrator.
- Click the "Install" button to save your changes.
- Open the administrative interface of the system. To do this, enter the address of the administrative interface in the address bar of the browser in the following format:
- In some cases, after installing the server part of the system, a message is displayed about the impossibility of starting ksrv.dll.
This situation can occur if the required certificate is not in the Trusted Root Certification Authorities store for the local computer. Update your operating system's root certificates (Internet connection required) or contact your service organization.
- The server part of the system does not have enough virtual address space when running in 32-bit operating system Windows.
The server part of the system can use up to 2 GB of memory, which it allocates and frees depending on the workload. If the database is large (more than 4 million documents), this amount of memory may not be enough. The size of the virtual address space can be increased up to 3GB using special boot options (keys).
For Windows Server 2008 (Windows Vista, Windows 7)
BCDEdit /set increaseuserva 3072
The BCDEdit utility should only be run from the command line. Command Prompt must be run as an administrator.
For Windows Server 2003 (Windows XP)
/3GB in the Boot.ini file
The following sample Boot.ini file excerpt illustrates the use of the option to allocate virtual memory:
multi(0)disk(0)rdisk(0)partition(2)\WINNT="Microsoft Windows Server 2003" /fastdetect /3GBSee the Microsoft Product Support Services article “Description of the 4 GB Memory Configuration Feature and the Physical Address Extension (PAE) Option” (http://support.microsoft.com/kb/291988/en)